Probe Kit
The Concept
The oil that drives the digital systems of our time is personal data, despite this fact many of us don’t really understand what this data is, how it’s collected/exchanged and how it’s turned into wealth. data security is a low priority for much of the popular software and hardware we use today, for this reason it’s very easy for institutions (large and small) with the right tools to collect and leverage much of your personal information. We set out to demonstrate this by collecting and focusing on one type of network data: probe requests. These are small messages your wireless devices emit into the air to connect to known WiFi networks. By collecting and algorithmically organizing this data and then cross referencing with other data we can create a profile (visualized as a butterfly) of the devices around you which includes all the networks a person has connected to and an interactive map for where these networks are (ie. where this person lives, works and plays) simply by listening to the data around us with generic wifi cards.
In order to generate interest in the topic, the team built an eye-catching user interface, where each mobile device that the system “catches” is turned into a virtual butterfly.The Result
Probe Kit debuted at the eMerge Americas Conference, as an activist “artware” installation aimed at illustrating how simple it is to collect personal network data and how much can be inferred from that data. Sarcastically pitched as an “amateur data collector kit”, Probe Kit was presented in three different forms: an app which turns your computer's wifi card into a “net” that catches the fluttering probe requests (data packets) emitted from the wireless devices of the people around you, an installation which collected and visualized all the personal data being collected throughout the duration of the conference, and a workshop where participants are given copies of the app and taken on an urban "data safari" where we collect this data together and discuss the implications.
the app
The Probe Kit app uses your computer's WiFi card to listen and collect all the probe request emitted by other phones and computers around you. In this initial device collection phase the app uses the MAC address of the captured devices (it's unique identifier) and WiFi network list size to generate a unique butterfly which represents that device. Every time a new device is captured a butterfly appears and flaps momentarily. If a butterfly continues flapping this means that this device is still around you and sending out probes (maybe someone sitting next to you?)

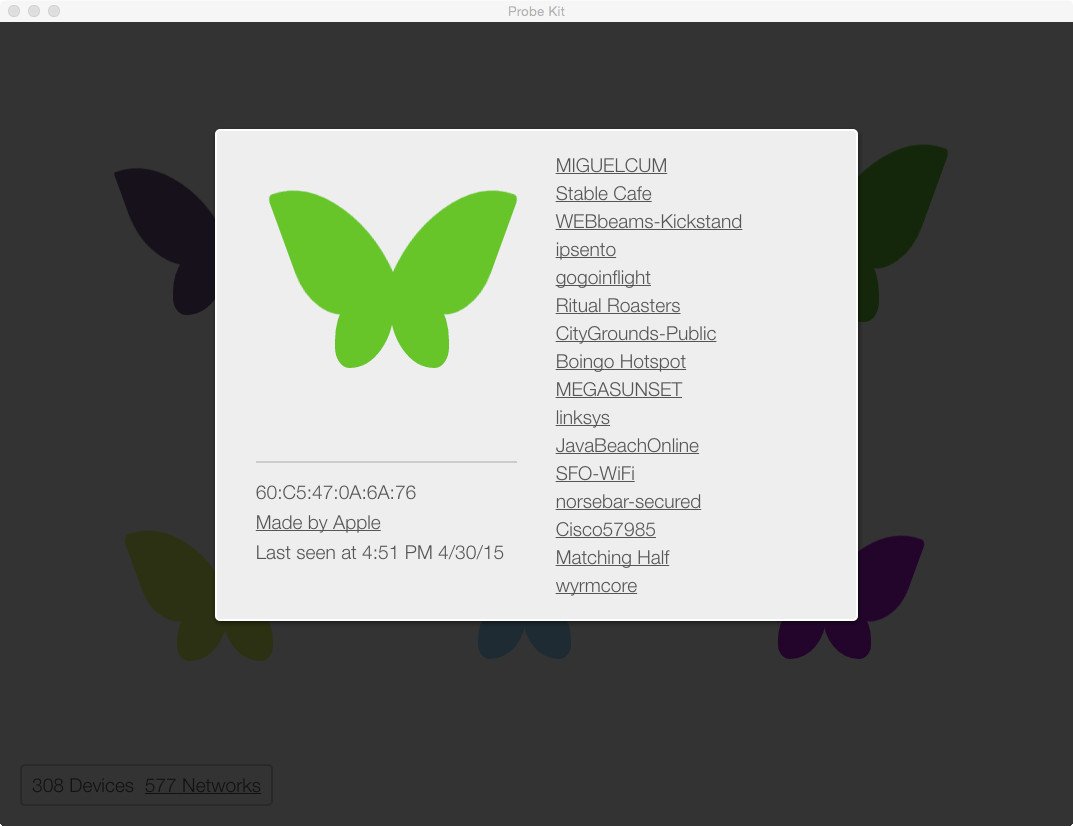
When you click on one of these butterflies (devices) an information panel displays the actual MAC address of this device, the vendor/manufacturer of the device (this can be inferred from the MAC address), when you last caught a probe from this device as well as the full list of WiFi networks this device has connected to in the past.
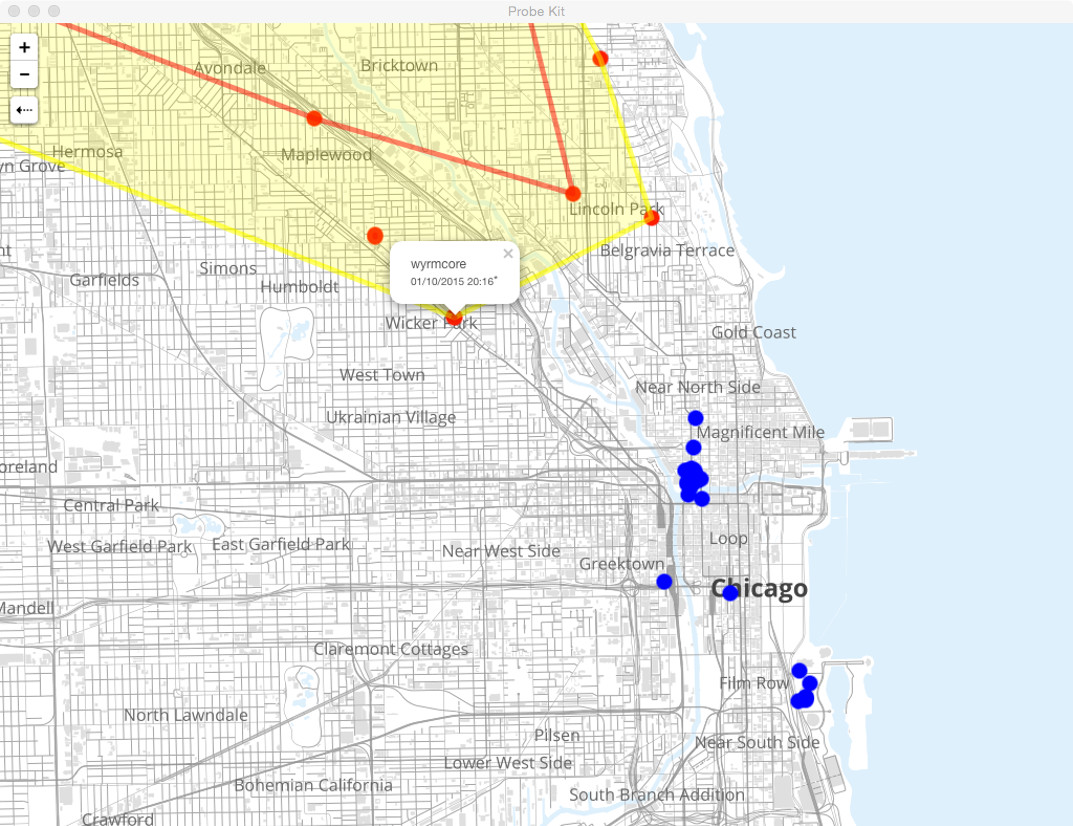
From there you can view the "migration patterns" of this butterfly on an interactive map. By cross referencing the list of associated WiFi networks with a dataset of geotagged wireless router beacon frames we can visualize where this device has been, or more specifically where this person has previously connected to a WiFi network.
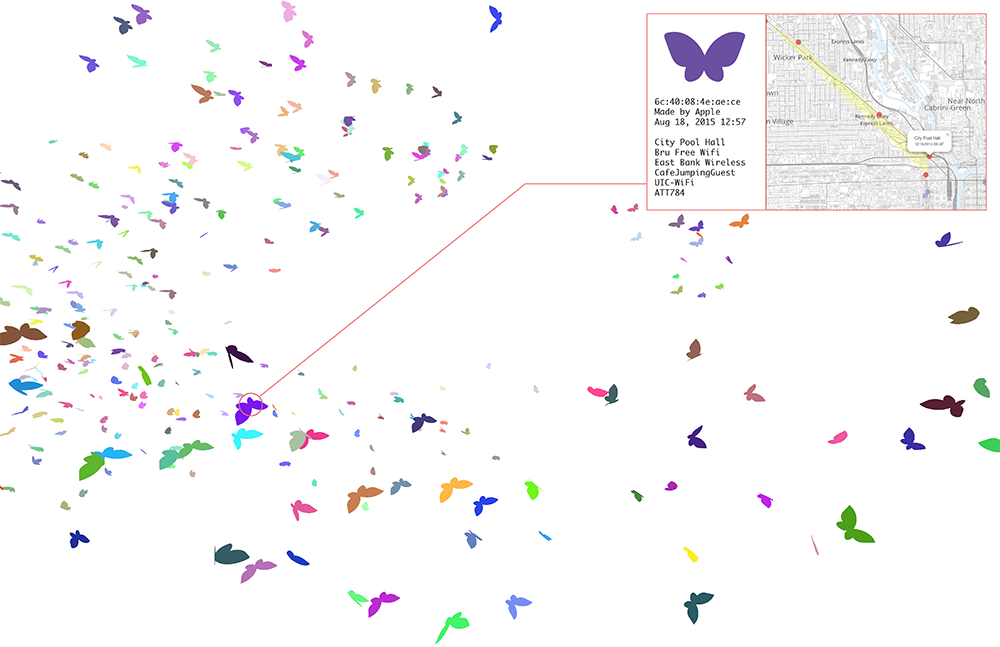
the installation
The Probe Kit installation debuted at the eMerge Americas Conference in Miami Beach and will be included at the International Symposium on Mixed and Augmented Reality in Fukuoka, Japan and later at the Radical Networks conference in New York City. A computer with a 9 dbi omni WiFi antenna collects probes from devices in the area while simultaneously spawning a butterfly per device in a projected “habitat” visualization. This installation view displays all the butterflies (devices) in a 3D space and scans for new devices and details their network list, map and related metadata.


the workshop
The “Network Data Safari” is a performative workshop where participants are given a copy of the Probe Kit app as well as “field guides” which explain how the app works. Participants take their laptops out into wild urban landscapes to capture probing devices and create their own network data collection. Together we analyze how it's possible to collect this kind of personal data and discuss the implications of being able to do so. At the end of the safari participants are encouraged to bring their laptops back to the installation to “release” their collection into the installation’s “habitat”, amassing an even larger data set.

